The field of Information Security always brings up images of hackers and crackers hacking and exposing systems. While it is entirely not false, there are plenty of ways and procedures to prevent these types of attacks or keep these attacks to a minimal level and improve the security of the organization. Some of them are “Pen testing” and “Threat Modeling”. While the main motive behind threat modeling and pen testing is to reduce attacks and make systems more secure, they differ in their approaches and when they are done.
Let us see more about Pen testing and Threat Modeling and their differences in this post:
Before we dig deeper into “Pentesting” and “Threat Modeling,” let’s just understand what “vulnerability” and “threat” are. In simple words, “vulnerability” is a flaw inside any system, and “anything which exploits the vulnerability” is termed as a “threat.
Pen Testing
“Pen testing” or “Penetration testing” is a simulated attack on a system and its defenses. Pen testers conduct various attacks against a system (similar to regular black hat hackers) which will expose the vulnerabilities of a system.
Normally, “pen testing” is carried out by outside contractors, since they will not have the idea of how organizational security measures are made up. These outside contractors are also called “ethical hackers. These ethical pen testers are going to attack the system with all kinds of strategies to break into your organizations systems. Normally, before a system goes into production, pen testing is done.
There are five phases involved in a pen testing process. They are listed as follows:
- Planning and Reconnaissance
- Scanning
- Gaining access
- Maintaining access
- Analysis and WAF configuration
After such vulnerabilities have been found, a report is created based on the level of vulnerabilities. Further, this report gives a guideline to the system administrator on how they can make the system strong enough by securing against any future attacks.
Here is a snapshot from a sample pen testing report
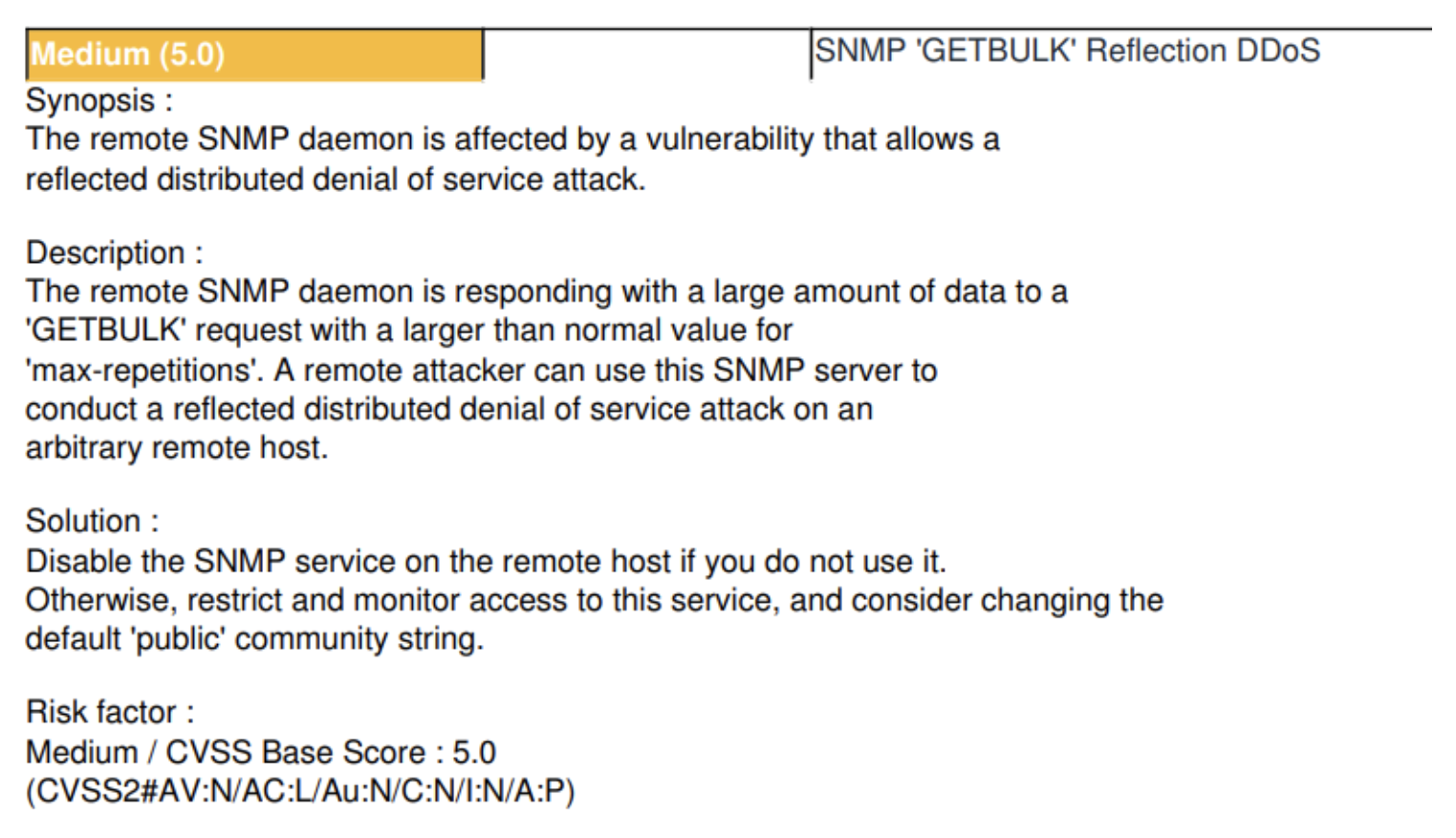
It also outlines the major risk factors, explains the vulnerabilities and provides mitigation strategies. When the fixes were implemented, the system should indeed be significantly more secure now.
Threat Modeling
The threat model activity is performed mostly at the design stage of the software development life cycle (SDLC); however, it can be conducted in other stages of SDLC as well. Threat modeling can be repeated as when there is a change in the design of the system; since business systems are constantly dynamic, this work is a continuous process done when.
- A new feature is released
- A security incident occurs
- There are infrastructure changes.
There are ideally four questions and answers that help us to organize threat modeling:
What are we working on?
We draw a Diagram to understand what we are working on
What can go wrong?
We try and understand the threats in this case
What are we going to do about it?
We try and mitigate the threats
Did we do a good job?
Next, we validate them to know whether we have done a good job or not” (Source: https://owasp.org/www-community/Threat_Modeling)
Once the threat model is created, imminent threats to system design can be reduced. There are several threat models that are prevalent in the industry today. Some of them are the PASTA, DREAD, STRIDE, and VAST threat models.
Also, read to comprehensively understand Different Threat Modeling Methodologies
Having seen what is meant by pen testing and threat modeling, let us see their key differences:
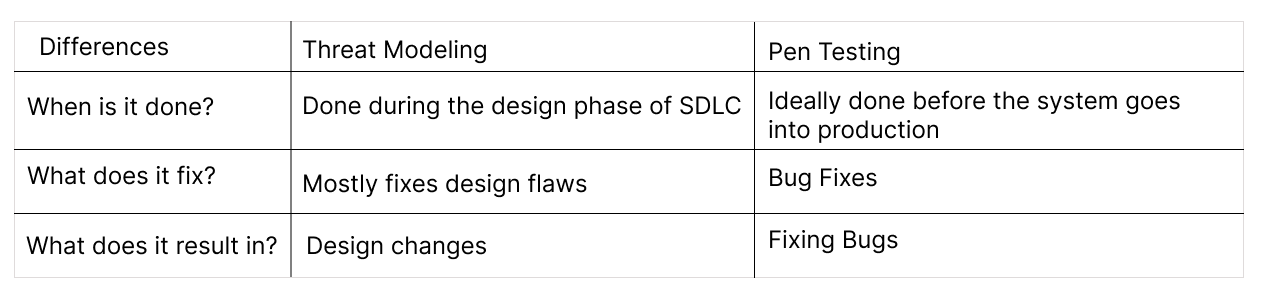
- Threat modeling is mostly done during the design phase of the SDLC. Pen testing is ideally done before the system goes into production.
- Threat Modeling mostly fixes system design flaws. Pen testing fixes bugs
- Threat Modeling results in design changes, while pen testing results in fixing bugs.
In spite of their differences, threat modeling can be used along with pen testing to make systems more secure!
We have seen the concepts of pen testing and threat modeling in this post along with their key differences. Join us as we uncover more in the DevSecOps space!
To know more information about our Threat Modeling course, do visit the ‘Certified Threat Modeling Professional’ (CTMP) course today!
References:






0 Comments