All Practical DevSecOps Courses will get a 15% discount during this Black Friday and Cyber Monday sale.
Why DFDs Rock for Threat Modeling
DFDs serve as maps, illustrating data flow pathways and exposing hidden vulnerabilities within your system. Here’s why they’re indispensable:
- Clarity: Visualizing the data journey facilitates the identification of weak points, from user input to the final output.
- Collaboration: DFDs provide a common language for security and development teams, fostering better understanding and communication.
- Proactive Defense: By analyzing data paths and potential attacker entry points, you can identify threats before they strike.
- Smarter Mitigation: Prioritize security measures based on identified risks and data sensitivity.
Building Your DFD: A Layered Approach
Let’s break down the process into manageable steps:
1. System Scoping
- Define system boundaries by outlining what’s inside and outside.
- Identify key components, including servers, databases, user interfaces, and external services.
Also Read, How to Improve Your Analytics Thinking in Threat Modeling
2. Data Flow Mapping
- Trace the path of data, visualizing where it enters the system, how it moves, and where it lands.
- Mark data stores, such as databases, logs, and temporary files.
3. Threat Identification
- Put on your attacker hat and consider potential threats at each stage of the data flow.
- Utilize STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial-of-Service, Elevation of Privilege) as a guide for identifying security risks.
Also Read, Threat Modeling vs Penetration Testing
Also Read, Types of Threat Modeling Methodology
4. Risk Assessment
- Analyze the impact and likelihood of each threat to prioritize security measures effectively.
- Identify countermeasures, including security controls and mitigation strategies.
Also Read, Best Way To Do Threat Modeling
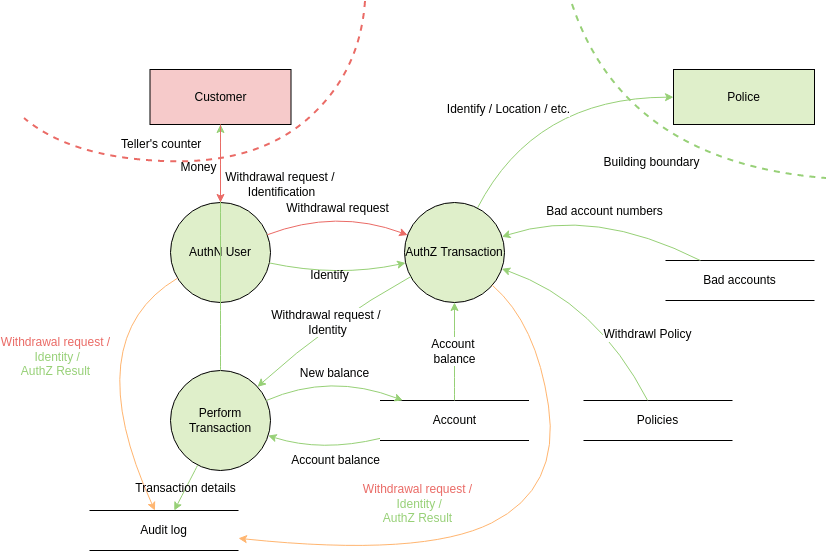
Real-World Example: The E-commerce Adventure
For instance, an online store where the user provides the credit card details and later, when the shipment is made, the payment processor will verify the details. A DFD of such a case will lay bare threats such as credit card skimming and order tampering. By analyzing these risks, the store can implement encryption, fraud detection systems, and secure data storage.
Example of a Threat Modeling Data Flow diagram
Also Read, Threat Modeling Best Practices
Conclusion
DFDs are dynamic documents that should evolve with your system. Keep them updated, share them with your team, and utilize them as a guiding compass through the ever-changing security landscape.
So, armed with your metaphorical markers, start mapping with DFDs. Illuminate potential vulnerabilities, build secure systems, sleep soundly knowing your data flows safely, and impress your fellow security nerds along the way.
Upskill in Threat Modeling






0 Comments