If you know the enemy and know yourself, you need not fear the result of a hundred battles ― Sun Tzu
A few years ago, I was doing a pentest and after spending 3 days, I couldn’t find even a single security issue.
As this has never happened before, you can guess my frustration.
Turnouts, I wasn’t doing two things.
One, I wasn’t following Sun Tzu’s wisdom.
“If you know the enemy and know yourself, you need not fear the result of a hundred battles”
I had knowledge but no wisdom. Wisdom is learning about the target before you attack it.
I spent the next two days learning about the app (as a user) and tried pentesting the app again.
Guess how many security issues did I find? a lot!
So before you learn how to attack containers, you need to understand a few things about containers.
- What is a container (Docker)?
- Why do we use it?
- Who uses it, where and when?
- How can Docker make my life easier?
So let’s dig in.
What is Docker?
If you are into IT or technology in general, you might have heard about Docker.
According to Wikipedia
Docker is a set of platform-as-a-service (PaaS) products that use OS-level virtualization to deliver software in packages called containers.
Sounds like watching a foreign movie with no subtitles right? Let me explain in simple terms.
Note: We will use the words container and docker interchangeably going forward.
So what exactly is Docker?
Docker is a containerization tool that helps you in creating, packaging and deploying applications.
Simply put ”instead of just shipping your application, you also ship the environment required to run the application”.
So fewer moving parts, fewer chances of disasters.
Why should you learn Docker?
So you may ask why should I Learn docker?
Let’s say, you are developing an application using python where you have to ensure that your application not only runs on your machine but works on the production system as well. But this application might work or might not, why?
Because the production system might have different versions of python installed on it or different versions of the python libraries/modules.
This is where Docker comes into play.
Container/Docker Advantages
Solves dependency collision.
Docker solves this problem. With docker, we can containerize the application with the required environment (os, libraries) and ship the application. Since it’s containerized into a single package, it won’t cause dependency collision issues.
Cross-platform
Since the same container image can be run on any Linux, Mac and Windows machine, Docker provides cross-platform compatibility and helps in easy deployment.
Write once, run anywhere!

Now you may say, I’m not a developer (but I’m into operations) so why should I learn docker?
Scalability
With docker, you can pretty easily scale your infrastructure as per your needs. If you are experiencing more load on your servers, you can increase the number of Docker containers. Similarly, if you are seeing less traffic, you might reduce the number of running containers.
Proper Resource Utilization
Unlike VMs there is no need to allocate extra resources (like RAM, CPU, and Disk) for OS. Containers use the host’s kernel features (like namespaces, Cgroups, etc.) to run the container.
Provides good security
Docker provides good security defaults and reduces deployment complexity, which helps in reducing the attack surface of Docker. We will discuss more security aspects as we move forward in this course.
Docker has many other advantages which is why top tech companies are using/have started using it.
These are some of the companies which use Docker’s container technology:
- Uber
- Visa
- PayPal
- Shopify
- Quora
- Splunk
Source : https://www.docker.com/customers
There are many startups that are slowly adapting the docker technology because of the above-mentioned benefits.
So if you wish to keep yourself updated with the latest technologies, it is important for you to learn docker.
Container vs VMs
But Imran, “virtualization already solves most of these problems, what benefits does docker bring to the table which Virtualization doesn’t? and why should I move to containers ?”
Let’s compare containers with virtual machines to understand the benefits of Docker.
In virtualization, each VM has its own guest OS/kernel. This is an advantage in itself, as the VMs are independent and isolated from the host system. However, this approach comes with a significant drawback of allocating additional memory and storage for each VM.
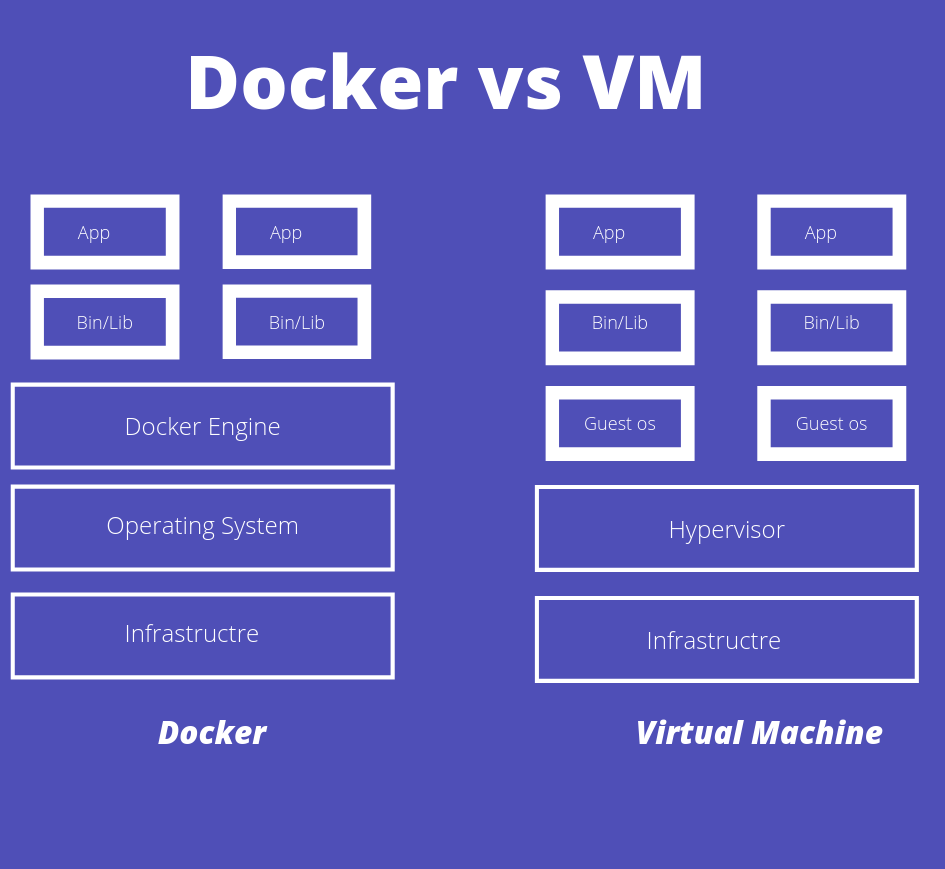
For example, you need to run 100 VMs simultaneously, each with 1GB of RAM, 1 CPU core and 20 Gigs of Disk.
1 GB * 100 = 100 GB
1 CPU core * 100 = 100 CPU cores
20 GB disk space * 100 = 2000 GB Disk
This increases the cost dramatically and reduces the performance of the overall system (hello, noisy neighbors).
Since container technology uses the host’s kernel features to run a container, there’s no Guest OS involved, which makes containers lean, fast and efficient than VMs as they have fewer layers compared to VMs.
So the saved resources can be better utilized to run more containers.
A picture is worth a thousand letters, let’s see an image which illustrates these points.
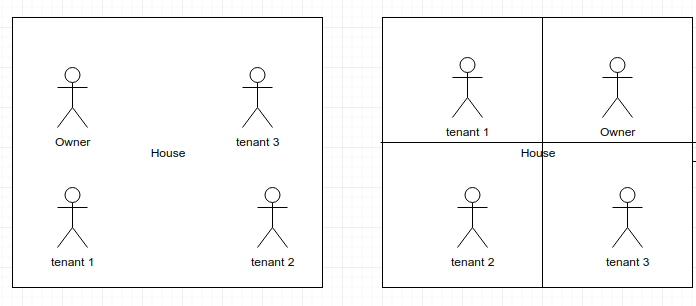
The first half of the image shows that the containers (tenants) share the same kernel (House) as the owner (Host OS).
In the second half of the image, VMs (tenant) do not share the same kernel as the owner (Host OS). Every VM is allocated a dedicated kernel and hardware resources (space), which cannot be used by other tenants (VMs).
Due to reduced overhead in the container stack, containers boot faster and are much performant than VMs.
In short, the container technology has more advantages than the Virtualization.
So does this make virtualization technology extinct?
No, Virtualization is here to stay, there are many scenarios where we prefer virtualization over container technology.
To sum it up, we have created a simple comparison table for you.
| VMs | Containers |
| Heavyweight | Lightweight |
| Has its own OS | Uses host OS |
| Takes minutes to start | Takes few milliseconds to start |
| More secure | Less secure* |
| Uses more resources | Uses fewer resources |
* An attacker needs to compromise both the guest and host OS to gain access to other VMs whereas in docker, just the host OS.
Docker/Container Disadvantages
People usually talk about docker advantage but no one talks about its disadvantages.
Like every other technology, Docker also has some disadvantages.
Poor GUI Support
Docker does not support GUI applications by default. There are some workarounds and hacks to overcome this issue but they are hacks, not features.
Poor Windows Support
Docker is a first-class citizen of Linux OS. Windows support is improving in recent times but it is far from Linux support.
Lack of mature Security tools
Lack of Guest OS in a container is both a boon and a curse at the same time. Boon, as it makes everything faster and efficient, but also a curse as exploiting a docker container might lead to system-wide compromise. Also, security monitoring tools for Docker are not as mature as non-container environments.
Lack of bare metal support
Docker needs host OS to work. It doesn’t run on the bare metal server like Type 1 Hypervisor.
Docker Architecture and its components
Let us now understand docker architecture and its components.
Docker’s architecture is pretty simple and it has two main components
- Docker Client (CLI)
- Docker Server (Daemon)
Docker Client (CLI) – The Docker client talks to the Docker Daemon and asks it to do some job on its behalf. For example, a client (CLI) can request details regarding running containers, the daemon responds with the states of the running containers.
Docker Server (daemon) – The Docker Daemon, is a background process that manages the docker images, containers, and volumes as shown in the below image.
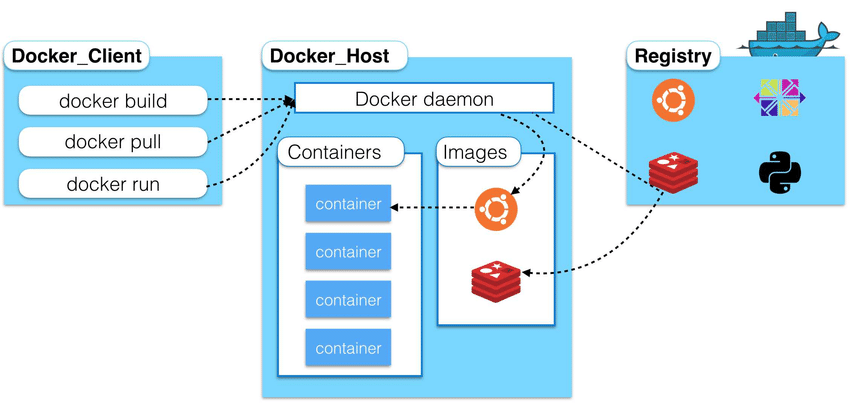
Source: https://www.researchgate.net/profile/Yahya_Al-Dhuraibi/publication/308050257/figure/fig1/AS:433709594746881@1480415833510/High-level-overview-of-Docker-architecture.png
Actually we lied, docker (> 1.11) is not so simple anymore.
Docker engine consists of many components (docker CLI, dockerd, containerd, and runC)
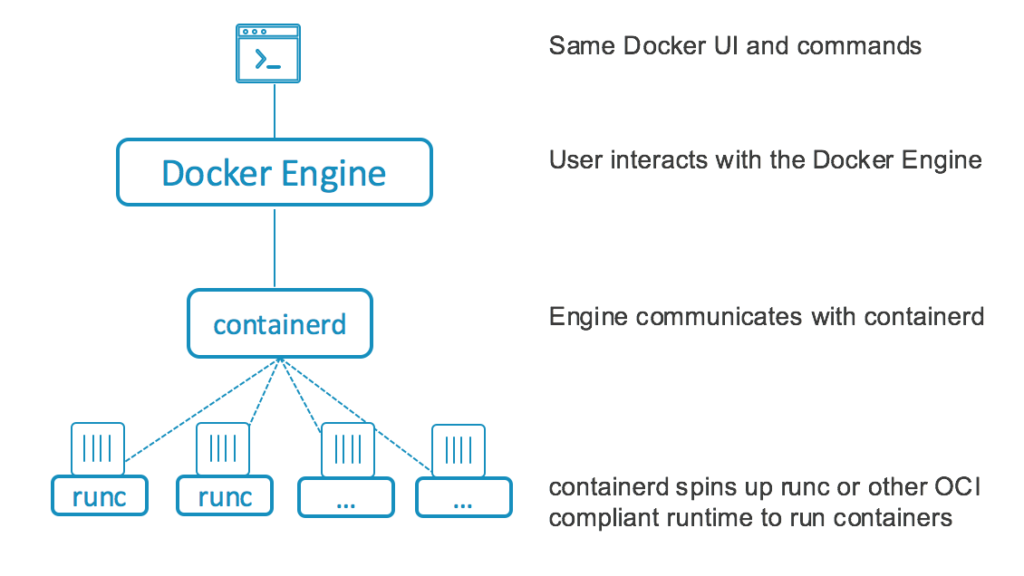
isn’t it awesome? besides the technological trivia that will impress your friends at a party.
This division helps you switch, a part of the stack with any other alternative and removes the dependency on one vendor (bye-bye vendor lock-in). For example, runC runtime can be replaced with CRI-O while still using dockerd and containerd from Docker.
What’s in it for me?
Docker’s Role in DevOps
Docker is heavily used in Agile, Continuous Integration and Continuous Delivery (CI/CD), Microservices and DevOps.
After developers finish testing the application, they package it into a container and then the Ops team will simply deploy the container.
Docker’s Role in Security Industry
Most organizations (if not all) are moving to container technology to help them achieve speed, scalability, and agility.
Obviously, the security industry needs to secure these environments, so there is an increasing demand for security professionals who understand Docker and DevOps, etc.,
Docker is heavily used to deploy security tooling in DevSecOps. We at Practical DevSecOps rely on docker to deploy various SCA, SAST, DAST, and monitoring tools for our clients.
Docker can also help you get few hundred to few thousand shells as part of post-exploitation 🙂
This week’s tasks
Each week, I’m going to share a lesson about Docker and then give you 1-2 hands-on tasks.
If you commit to doing the work, you will get the results you want.
This week we are going to do two tasks.
- I only covered “Know thy enemy” but knowing yourself is the second most important thing, which I wasn’t doing. The more you set your intention, the more likely you are to get it. Share what inspired you to learn Docker and what you would like to get out of this course by commenting here and you can also interact with your fellow professionals here.
- Set up the lab environment in your machine.
Lab Setup for the Docker Security Course
Didn’t we say, this course is going to be hands-on and practical? let’s go ahead and set up a lab for this course.
If you are our paid customer and taking any of our courses like CDE/CDP/CCSE/CCNSE, please use the browser based lab portal to do all the exercises and do not use the below Virtual Machine.
Before proceeding, please ensure hardware and software prerequisites are met.
Software and Hardware requirements
Hardware
- Laptop/System with at least 4GB of RAM, 15 GB free hard disk space and should be able to run a Virtual machine.
- Administrator access to install software like Virtualbox, Extensions, etc., and to change BIOS settings.
Software
- Virtualbox, you can download VirtualBox from here.
- Docker Security Course OVA file
Extra: If you are new to VirtualBox and want to know more about installation and usage you can refer following links.
Note: Please restart your machine after the Virtualbox installation.
Now that we have installed Virtualbox and downloaded course OVA file. Let’s configure the course virtual machine by following the below steps.
Step 1: Open Virtual Box
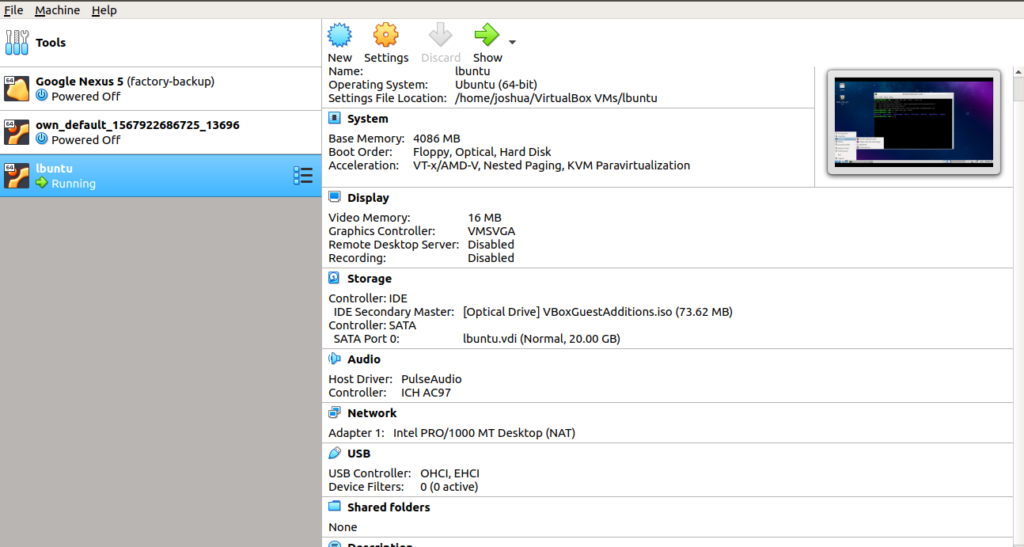
Step 2: Click on file > Import appliance
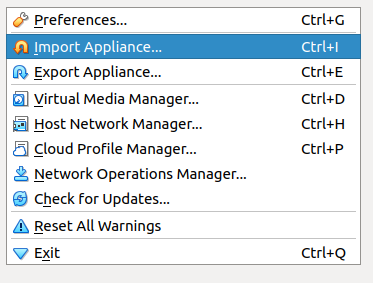
This will open a pop-up.
Step 3: Click on the file browser icon on the right side
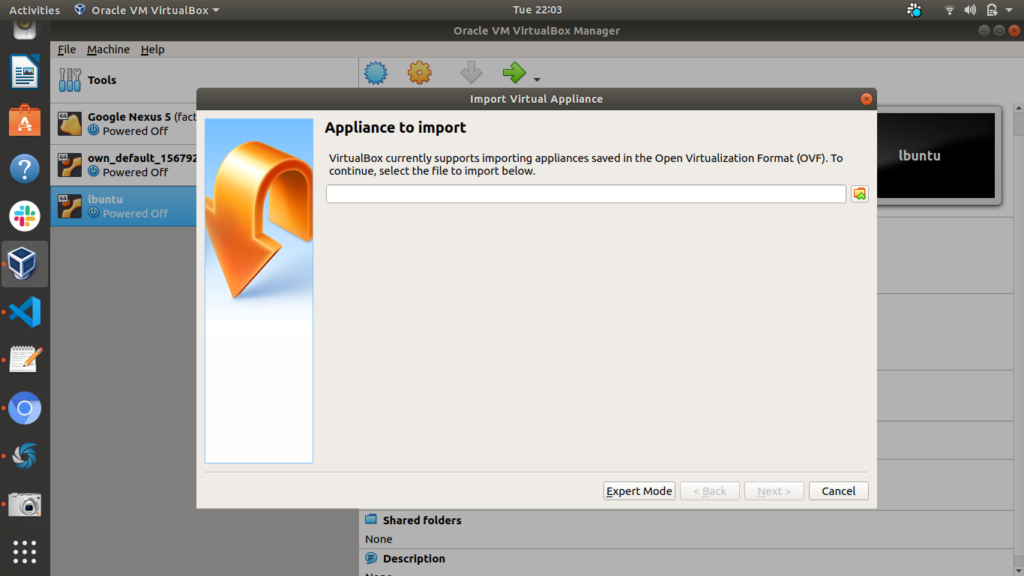
Step 4: Select the downloaded ova file (which you have downloaded from the software requirement section above) and click open
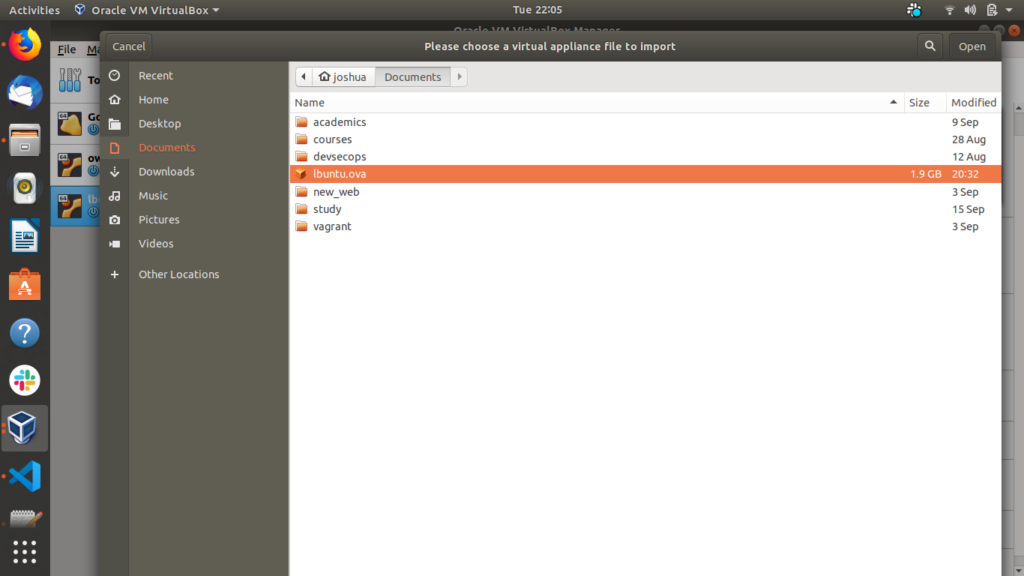
Step 5: Next click on the import button.
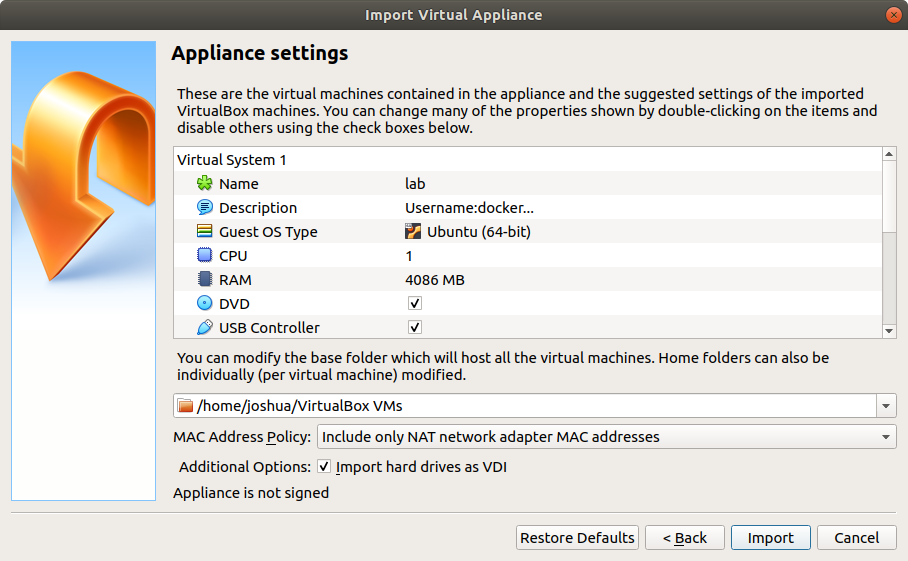
Step 6: Once the file is imported select the lab image and click on the start button.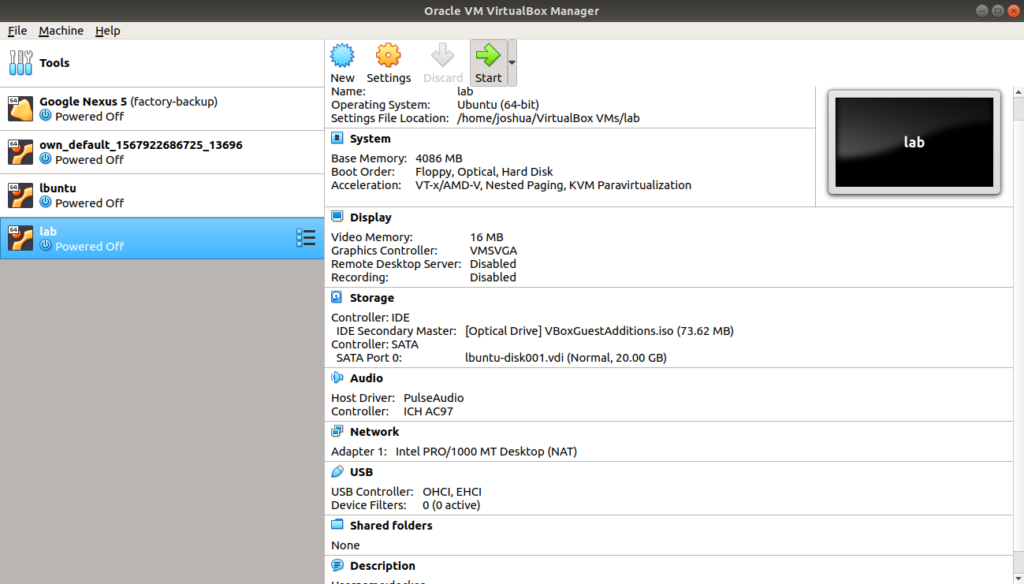
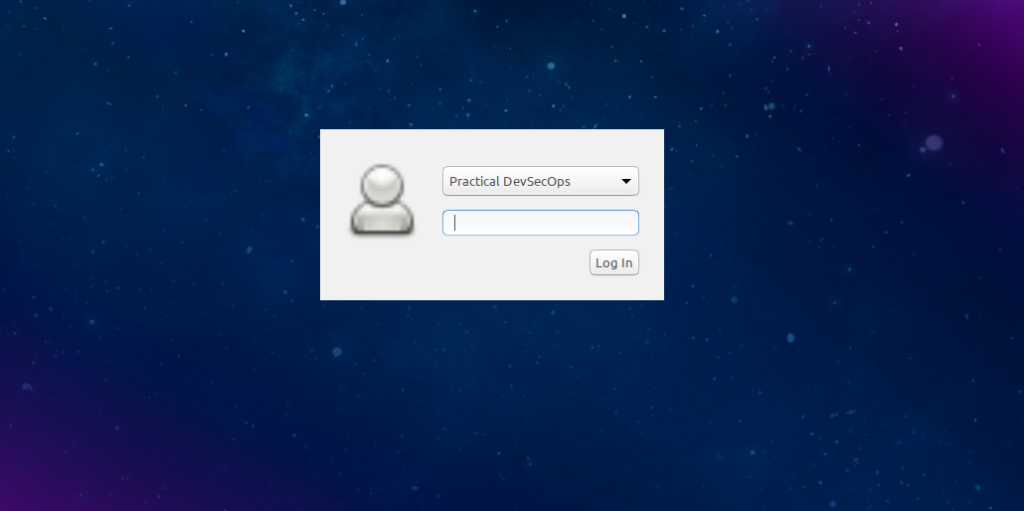
Step 7: Once the VM finishes booting, login to the lab using the following credentials.
Username: practical-devsecops
Password: docker
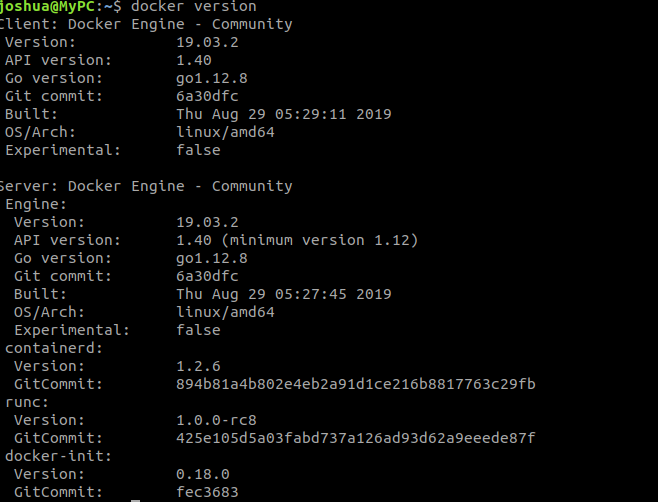
Step 8: Verify the installation of the required software and packages by running the following commands one after the other.
Open a Terminal (aka command prompt) by clicking on the Menu → System Tools → LXTerminal
To verify the installation of the docker, we can use the following command.
$ docker version
As a software industry tradition, we will start with a customary “Hello-world” image.
Open up the Terminal and type the following command.
$ docker run hello-world
Once the command finishes, you will see the output as shown below.
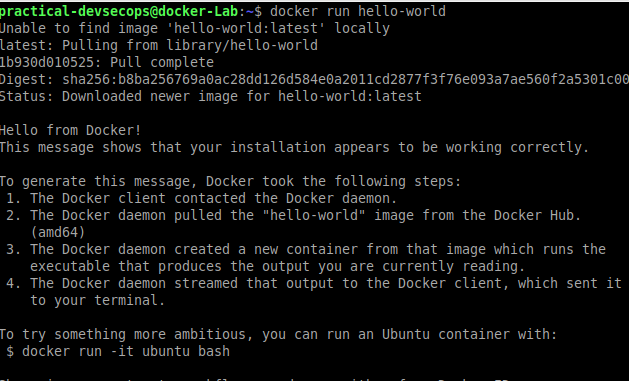
That’s it for this week’s tasks.
Reference and Further Reading
- Docker getting started page https://docs.docker.com/get-started/
- Docker announces modular docker-engine design with dockerd, containerd and runC https://blog.docker.com/2016/04/docker-engine-1-11-runc/
- History of container technology https://opensource.com/article/18/1/history-low-level-container-runtimes
Conclusion
Today, you saw how powerful containers are and how you can leverage them to go to market faster. Using container technology, businesses can go to market faster, gain more customers, generate more revenue, provide employment to more people and create wealth for their nations.
We have also configured the lab environment for our future docker security lessons.
Next week, we will learn the technical nitty, gritty details of Docker like Docker Layers, Images, Containers, Registry and much more.
Please stay tuned for our next lessons.
Looking forward to seeing you next week, have a great week ahead.
Best,
Imran and the Team
Ishaq, Joshua, Mohamed, Irfan.
P.S. Remember, leave a comment here, we are curious to know what you would like to get out of this course.






This lesson is awesome, very understandable for me. But I have a question for setup the lab. The .ova file OS is Ubuntu 64-bit. Unfortunately, my processor is old enough to be able to virtualize 64-bit OS. Can I ask 32-bit version of Docker Security .ova file?
Thanks for your attention 🙏
Hi Ramadhan,
Thank you. We will try to setup a 32-bit version next week, we will email you once we have created a 32 bit version.
Hey Imran and team, Great course and looking forward to the next lesson.
BR,
Georges from Belgium.
It’s always great to hear from you Georges 🙂
hi imran, looking forward for more. actually started learning docker a while ago. As a pentester wants to learn docker and docker apps pentesting.
You will be pretty happy to see our upcoming lessons, we are excited to share future lessons with you. Thank you.
Hey Imran and team,
Very well explained, looking forward for the next class.
Glad you enjoyed our the first lesson.
Hi Imran
This course is inspiring. Waiting for next week.
You made our day, thank you Tharun
Hi Imran,
I could not able to view everything in official mail id.
is there any chance to update personal mail id to get the course there.
Thank You…!!!
Hi Sharath,
Sorry to hear about it.
For exactly this reason, we have also included online version of the email, you can click on the first link. It will take you to the online version of the class.
Please let us know if you face any other issues.
Thank You Imran
Hi Imran,
Thanks for the course. It is really nice.
Looking for more practice session in coming lectures.
Thank You!
Our website name has practical for a reason 😉 Thank Rukender.
Hi Imran,
in advance thanks for this great course.
Thanks for your time dedicated to this, and for sharing the information,
I learned a lot, waiting for the next lessons,
Hi Agim,
Glad you enjoyed this lesson.
Great course. Look forward to the next lesson
Thanks, please do help us spread the word about the next batch using this link – http://free-courses.practical-devsecops.com/docker-security-course
Though I know Docker, I learned new things with this document. Thanks to Imran, for sharing the importance of docker in day to day life.
Great explanation.
An attacker needs to compromise both the guest and host OS to gain access to other VMs whereas in docker, just the host OS.
I’m happy you liked it Khamruddin
Great explianation, thanks Imran
Thanks for your comment.
Great course. i’m new in this and i can understand this quickly,,
thank you so much
I’m glad you liked it Chandra.
Hi Imran & Team,
Great article(lesson) for beginner level. Waiting for the next lesson.
Thanks 🙂
Hey Amar, happy you liked it. Please do check out lesson 2
Great course, waiting to dig in the following lessons!
Hi Itay,
I’m looking forward to have you in the course till lesson #12(I saw your comment on lesson #2)
Lesson#1 well written.
Registered to learn.
Appreciate it Alexandre.
Good, concise and straightforward introduction! Waiting to learn more.
Sreeman, good to see your comment here buddy 🙂
Not displaying the login page after import the OVA in Oracle VM. showin block screen only, even tired other system also.
Kanan, it might be because of BIOS settings of your system, please enable virualization, and do let us know how it goes.
Tutorial to enable Virualization:
https://support.bluestacks.com/hc/en-us/articles/115003174386-How-can-I-enable-virtualization-VT-on-my-PC-
(See section 2.2 Enter PC BIOS)
Explanation is very detail and easy to understand which made to look forward for learning more
We hope to keep our content quality up 🙂 please keep sharing your feedback with us.
Good intro to dockers, waiting for the next lessons. Thanks Imran & team.
Next lesson is already out Raja, please check your email for lesson #2
Hi Imran,
I was on the course you ran at DevSecCon in London last year, I thought I needed a refresher, and am so glad I did, once again, a very interesting and informative course.
Was interested in forwarding the lessons on to my colleagues, would that be OK, or would it be better for them to sign up too?
Again, many thanks.
Andy
Hi Andy,
Good to hear from you again and hope you are doing good.
We are always adding new content like cheatsheets, Infographics etc., so I think your colleagues will have better experience signing up for the email course.
Sign up URL:
https://www.practical-devsecops.com/pre-signup
Thanks for checking out our course Andy
Well written. Waiting for the next lesson.
Lesson 2 is already out, please check your email.
Excelent course 🙂 I’m really interested in learning about DevOps and security!
Glad you liked this course, please do let me know how we can help 🙂
Very Informative .
Thank you Krishna
Hi, I am getting the following error and could not able to resolve this..
VT-x is not available. (VERR_VMX_NO_VMX)
Enabled VT-x in BIOS and Disabled Hyper-V virtualization in windows features. But still the same issue..
Could anyone help me with this..
Hello Imran and Team,
I’m very happy to learn Docker!
Salams Imran. This was really good. The content was well explained and the screenshots were perfect. Good start to learning this for me. looking forward to the next session.
Hi Imran,
Thank you for the wonderful first part. i have read more on docker and also found out that docker has one more disadvantage that we cannot find the user who deletes the container and spins up. For that i found podman. will it be useful if we add a session on podman vs docker.
@nullhyd
Really a good intro to docker
Hey Imran and Team,
It is great to see the first email of the course. It was very nicely written and and newbie to Docker was able to wrap my head around the idea. As there is always a room for improvement, I believe a little introduction to Docker over Windows would have been useful too. I am impressed with the way the concepts are presented in this email. Thank you
Its very interesting topic and you hvae articulated it well. Lab will be helpful to understand better
Hello: Imran
Well written and great contents. Looking fordward to learn more. When i start the vm i get a console view not the graphic and the user and password is not valid….
Please forget: My mistake wrong vm
When i start the vm i get a console view not the graphic and the user and password is not valid….
Awesome course. Very informative. I was always curious to know what all the fuss was about with dockers. Good one.
Got lesson 1 in email but did not receive any email after that.
Kitap Indir En Son Okunan Romanlar
You need to reduce the ram to 3GB
Hello Imran I am unable to open the vm even after enabling the virtualization in the bios. Please help setting it up
Thanks Imran for making me part of this learning. It’s very informative and the explanation is clear enough for a nom technical person like me to understand. Looking forward for more !!
Hi Imran,
Wonderful training and good start with the introduction to docker. Looking forward to move to securing docker too with your great training.
Thanks
Chaminda
Awesome, thanks for the courses
The content was really nice and very deep about docker and its initial lab setup
Its really helpful I’ve known to use dockers and where to apply them
Hey thank you so much! It was a lot of information in just one lesson. Looking forward to receiving more. Thanks for the course.
A general curiosity in tech and learning about devsecops
Excellent content. Looking forward for next session.
The course looks promising, looking forward for the next chapters. Congratulations and thank you for making it available for free
I want to learn docker because of the simplicity to start an application, in the past, we need to install several dependencies. With this course, I want to deeply understand the main components to work with security aspects.
I want to understand this new world of containerization, microservices, orchestration etc so that I can port the “traditional” security knowledge to this new era.